SSL (Secure Sockets Layer) is a protocol that encrypts information between two specific points, like a server and a client. Clients can be browsers or other type programs such as Windows Update. An SSL protocol works above a Transmission Control Protocol (TCP), the set of networking systems in place to allow computers to communicate, and below protocols such as HTTP. Generally, when a website needs an SSL connection, users can see this by the url, which typically begins as HTTPS.
SSL provides a secure method of sending sensitive data from one party to another. SSL is also in place to detect when data or certain parts of what is being sent over has been altered; it also secures data in such a way that attackers or other third parties cannot read the data being exchanged. SSL is layered. Data sent under an SSL protection is divided into records.
How do SSL Certificates Work?
SSL operates on a cryptographic system with a public key and a certificate. The client begins what is called the SSL “handshake” – sending out information to the server such as what level of SSL it is using and what cipher suites (a combination of authentication, an encryption message verification code and key exchange algorithms) and compression manners it desires to use. A handshake wants to establish the items needed to send over messages, such as keys and algorithms and other specifics. The server then uses the highest version of SSL both it and the client can support and combines that with a compression method and chosen cipher suite to send over a certificate.
An SSL Certificate consists of domain title information, the name and location of the domain’s owner and the dates in which the certificate is valid. The certificate must be honored and verified by the client. Once the certificate is verified, the public key is swapped. Both the server and the client change the key for encryption – this creates a trusting relationship between the two, where now the server knows that anything shared from that client will be encrypted. To finalize things, the client sends the server an encrypted, authenticated message, which the server verifies is correct and is able to be decrypted. It returns the message to the client to be verified again.
It is at this point that the “handshake” is complete. The connection is closed securely using a special alert. What happens if a hacker tries to disconnect the two remotely? The connection will only be interrupted, not put into jeopardy. An attacker will try to close the connection by ending the TCP connection – and both sides will be notified and aware of this.
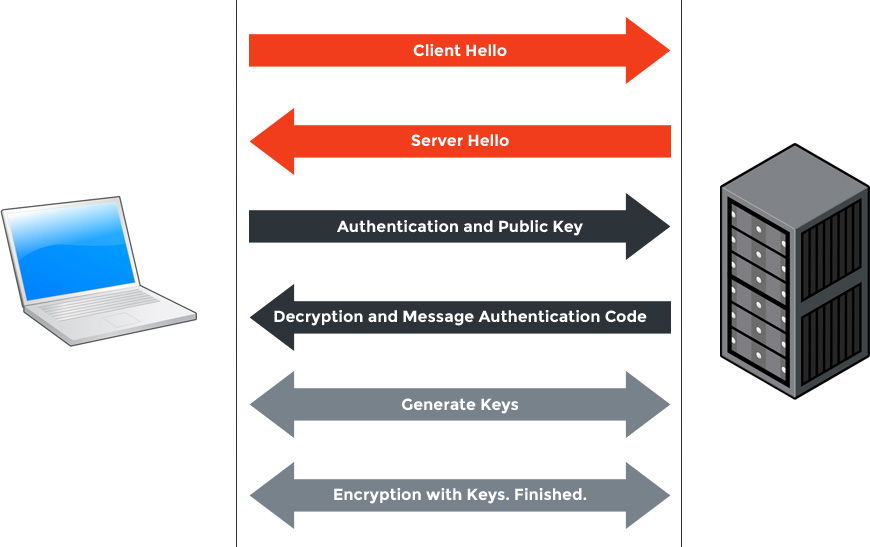
An SSL handshake looks like this:
- Client Hello
- Server Hello
- Authentication and Public Key
- Decryption and Message Authentication Code
- Generate Keys
- Encryption with Keys
Public and Private Keys
The cryptographic system creates two keys to encrypt data. One key is a private key (the certificate), generally known only by the recipient – in the above example, that would be the server. The other key is a publicly known key. Ordinarily, the public key operates to encrypt – the private key is in place to decrypt. Yes, anyone can make a public key and private key that work together. It is very important then that the public key is trusted.
In addition, key size comes into play. The larger and more detailed both the public and private keys, the more difficult it is for an attacker to break the key sent from the client to the server.
How Can Attackers Attack SSL?
 An SSL is in place because when it is being used in the right manner, the only things that are visible to hackers are IP addresses, a small amount of data and what encryption and compression methods are being used. Hackers can then interrupt the connection but, as stated above, both parties will know that it was neither of them who tried to close it.
An SSL is in place because when it is being used in the right manner, the only things that are visible to hackers are IP addresses, a small amount of data and what encryption and compression methods are being used. Hackers can then interrupt the connection but, as stated above, both parties will know that it was neither of them who tried to close it.
If an attacker knows both a public and private key, he can use the private key to sign any certificate. Then when an artificial certificate is sent over, the client will not know that it is from a fake public key and stolen private key. However, the server’s public key protects itself after it has been verified that it actually belongs to the server. It is encrypted. Only can the receiver of the private key decrypt it. This is why large key size is essential.
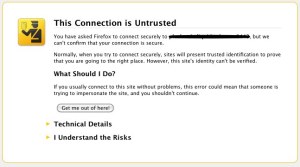
Attackers can try to get in when a person chooses to ignore a certificate warning that pops up on an unverified site. Ignoring the warning does not allow an SSL to work. When this occurs, a hacker can send over a certificate he developed, not necessarily one that he forged. In addition, servers and clients can have built in flaws, or flaws about which they were not aware, that can cause SSL to fail. One of these flaws is when a HTTP does not have a secured login page and changes to an HTTPS page. SSLstrip, a device that changes the insecure login page so that it defers to a page where anyone can obtain it.
SSL is Still Dependable
When an operating system goes into place, a record of all dependable Certificate Authorities (CA) was most likely installed with it. This is a record of public keys. It can be adjusted according to you and your preferences, but the list, of course, is endless and constantly changing. Though yes, you will trust any website that’s on that list, the organizations behind it are constantly being audited and checking that sites are trustworthy. A certificate is only issued if the person who registered it can prove they are the owners of the domain it was registered for.
SSL and its many layers are not flawless or mistake-proof, but correctly-developed SSL is secure on a very common, very reliable basis. Unfortunately, human error and human wrongdoing will always be a factor. These reasons may be why relying on SSL is so important. Common browsers are also protected against larger attacks and are constantly being updated to have protection in place against further threats.